Cybersecurity
Protecting the game: Fighting piracy to keep African football alive

On the evening of 21 December 2025, a football match will kick off between Morocco and Comoros in Rabat. It will be the opening game of the 35th edition of the TotalEnergies CAF African Cup of Nations (TotalEnergies CAF AFCON) tournament. The game will have an audience of millions.
There will likely be a full house of 68,000-odd fans at the Prince Moulay Abdellah Stadium, but the overwhelming majority of fans will watch the game via streaming and television, from across the African continent – and the world.
At the previous TotalEnergies CAF AFCON tournament in 2024, the semi-final match between South Africa and Nigeria had a record-breaking audience (https://apo-opa.co/4rJl26Z) of 10.3 million. The tournament itself had an estimated cumulative total viewership of 1.4 billion TV viewers.
The sale of broadcast rights to reach this enormous audience provides the income that makes the tournament possible. Media businesses invest billions in securing the feed for their home markets. In sub-Saharan Africa, those rights (https://apo-opa.co/4iGjuXm) have been secured by MultiChoice, a CANAL+ company, through SuperSport, its sports broadcasting affiliate.
Beyond rights payments, media investment sustains an entire economy that runs for the duration of the month-long tournament. Film crews, accommodation, logistics, and catering are hired by broadcast teams.
Media funds football
Broadcast licence fees also finance the Confederation of African Football (CAF) itself, the body that administers football on the continent. In many ways, media coverage funds football. Revenue from broadcast rights underpin the development programmes that find talent at youth level, and help to nurture it.
Media income funds infrastructure that makes football possible – the fields, the kits, the match officials, the transport, the administrators. At the top level, media income funds national teams, the coaching teams, and the elite training camps, so they can attend the continental showpiece, where they carry hopes and dreams of their nations.
However, the entire football edifice is a precarious one, heavily dependent on the ability of official media partners to recoup the multi-million-dollar costs of broadcast rights. If broadcaster income from subscriptions, contracts and pay-per-view sales does not cover rights fees, then ultimately, football dies.
Only large media businesses, with the advantage of regional scale, are able to fund the costs of media sports coverage. Perversely, their business model is threatened because the same sports events they bring to their viewers are prime targets of content piracy.
Viewers might not see the harm of accessing a pirate stream, but the impact runs deep. Where a subscription paid to a legitimate rightsholder would help to fund African football, any income earned by a pirate stream goes directly to criminal syndicates in other parts of the world.
Content piracy undermines football. It robs football associations of the funding they desperately need to survive, to develop youth structures and to compete at the highest level. It's therefore critical that sports fans understand the damage they do to the sport they supposedly love when they use pirate streams.
The impact is global. In Spain, LaLiga (https://apo-opa.co/4oC1TRL) reported that audiovisual fraud was costing Spanish football €600 and €700-million. In the UK, the Premier League blocked more than 600,000 illegal live streams (https://apo-opa.co/4pt6VRU) in a single season in its fight against piracy.
Pirate websites also place users at risk, exposing them to malware, hacking and identity theft, as well as unwanted pop-ups, viruses, fraud and adult content. When football content is spread across hundreds of thousands of sites, it also becomes harder to measure audiences, and makes the sport less attractive to sponsors.
Fight to save the game
Helping to fight sports piracy and keep football alive are initiatives such as Partners Against Piracy, which work to strengthen legal frameworks to prosecute pirate sites and pirate users, and to educate fans about the consequences of piracy.
Cybersecurity organisations like Irdeto harness tech and digital solutions (https://apo-opa.co/4aB6nog) to protect streams and track the source and the users of pirate feeds. For instance, a new innovation enables continuous renewal of authentication keys, which degrades the pirate experience and shifts users back to legal platforms.
The best partner in the fight to save football from piracy is the African public. Knowing how piracy destroys the football ecosystem empowers fans to make ethical choices in how they support their sport and makes them more likely to access games through legitimate channels.
As a fan, when you watch football content, the choice is yours: Will you be part of destroying football, or building it up? Choose wisely, the future of your sport depends on it.
- To report content piracy, contact Partners Against Piracy on any of these channels:
- International Hotline: +27 11 289 2684
- piracy@multichoice.co.za
- mcg@irdeto.com
- supersport@irdeto.com
- Visit: https://apo-opa.co/44KEGpm
The number of the year: Kaspersky detected half a million malicious files daily in 2025
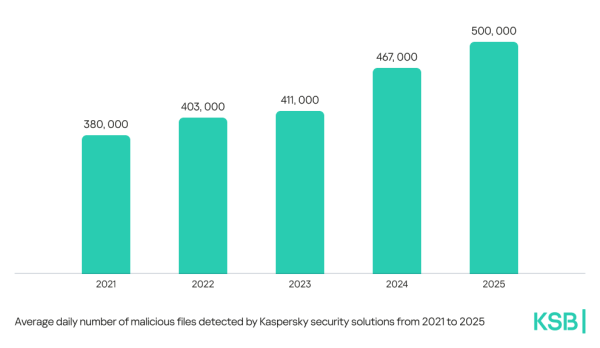
Kaspersky's (www.Kaspersky.co.za) detection systems discovered an average of 500,000 malicious files per day in 2025, marking a 7% increase compared to the previous year. Certain types of threats saw growth globally – there was a 59% surge in password stealer detections, a 51% growth in spyware detections, and a 6% growth in backdoor detections compared to 2024.
These findings are part of the Kaspersky Security Bulletin (https://apo-opa.co/44CY5Zj) series where we review the key cybersecurity trends of the past year.
Windows remains the primary target for cyberattacks. 48% of users on Windows were targeted by different types of threats throughout 2025. For Mac users, this figure stands at 29%.
Web threats
Globally, 27% of users were attacked with web threats – these refer to malware that targets users when they are online. Web threats are not limited to online activity, but ultimately involve the Internet at some stage for inflicted harm. In Latin America, 26% of users were attacked by web threats in 2025, while this share reached 25% in Africa, 21% in Europe and 19% in the Middle East.
On-device threats
33% of users were attacked with on-device threats. These include malware that is spread via removable USB drives, CDs and DVDs, or that initially makes its way onto the computer in non-open form (for example, programs in complex installers, encrypted files, etc.). Africa headed the rating with 41% of users attacked with this type of threat; APAC reached 33%, Middle East – 32%, Latin America – 30%, and Europe 20%.
“The current cyberthreat landscape is defined by increasingly sophisticated attacks on organisations and individuals around the world. One of the most significant revelations made by Kaspersky this year was the resurgence of the Hacking Team after its 2019 rebranding, with its commercial spyware Dante used in the ForumTroll APT campaign, incorporating zero-day exploits in Chrome and Firefox browsers. Vulnerabilities remain the most popular way for attackers to get into corporate networks, followed by using stolen credentials – hence the rise in password stealers and spyware we see this year. Supply chain attacks are also common, including attacks on open-source software. This year the number of such attacks increased significantly, and we even saw the first widespread NPM worm Shai-Hulud,” comments Alexander Liskin, Head of Threat Research at Kaspersky. “This increasingly complex threat landscape makes implementing robust cybersecurity strategies vital for organisations, as failure to do so can lead to months of downtime in the event of attacks. Individual users should also always use reliable security solutions, otherwise they put not only their data and money at risk, but also those of the organisations where they work.”
Follow this link (https://apo-opa.co/44CY5Zj) to learn more about other KSB reports.
To stay protected, follow the recommendations below.
Individual users:
- Do not download and install applications from untrusted sources.
- Do not click on any links from unknown sources or suspicious online advertisements.
- Always use two-factor authentication when available. Create strong and unique passwords, using a mix of lower-case and upper-case letters, numbers, and punctuation. Use a reliable password manager to help to remember them.
- Always install updates when they become available; they contain fixes for critical security issues.
- Ignore messages asking to disable security systems for office or cybersecurity software.
- Use a robust security solution appropriate to your system type and devices, such as Kaspersky Premium (https://apo-opa.co/4pFVUMB).
Organisations:
- Always keep software updated on all the devices you use to prevent attackers from infiltrating your network by exploiting vulnerabilities.
- Do not expose remote desktop services (such as RDP) to public networks unless absolutely necessary and always use strong passwords for them.
- Use advanced Kaspersky Next (https://apo-opa.co/4pQstI1) security products for comprehensive visibility across all company's corporate infrastructure to rapidly hunt out, prioritise, investigate and neutralise complex threats and APT-like attacks.
- Use the latest Threat Intelligence (https://apo-opa.co/3MdQvOI) information to stay aware of actual TTPs used by threat actors.
- Back up corporate data regularly. Backups should be isolated from the network. Make sure you can quickly access the backups in an emergency if needed.
All statistics in this report come from Kaspersky Security Network (KSN). For 2025, the statistics cover the period from November 2024 through October 2025.
Distributed by APO Group on behalf of Kaspersky.For further information please contact:
Nicole Allman
nicole@inkandco.co.za
Social Media:
Facebook: https://apo-opa.co/4iwRZzo
X: https://apo-opa.co/4owAi4r
YouTube: https://apo-opa.co/48pGVkt
Instagram: https://apo-opa.co/3XwhmI4
Blog: https://apo-opa.co/4apW9XJ
About Kaspersky:
Kaspersky is a global cybersecurity and digital privacy company founded in 1997. With over a billion devices protected to date from emerging cyberthreats and targeted attacks, Kaspersky's deep threat intelligence and security expertise is constantly transforming into innovative solutions and services to protect businesses, critical infrastructure, governments and consumers around the globe. The company's comprehensive security portfolio includes leading endpoint protection, specialized security products and services, as well as Cyber Immune solutions to fight sophisticated and evolving digital threats. We help nearly 200,000 corporate clients protect what matters most to them. Learn more at www.Kaspersky.co.za.
Artificial Intelligence (AI)-powered water management research and development (R&D) to strengthen water security in South Africa

A leader in industrial automation and digital transformation solutions for over 30 years, Adroit Technologies (https://AdroitSCADA.com/) is advancing its cutting-edge research and development (R&D) into an AI-powered Water Management Platform, designed to tackle one of South Africa's most urgent infrastructure challenges: non-revenue water losses.
The R&D presents an opportunity to develop a first if its kind, AI-driven ‘pseudo-metering' capability, a potential breakthrough feature that can infer consumption and pressure data in areas where physical meters are not installed. “We have proven the initial concept and have now secured the support of the government and other industry leaders to develop this AI-driven platform, confirms Frits Kok, Co-CEO at Adroit Technologies.
With nearly 40% of the country's treated water lost to leaks, theft, and ageing infrastructure, Adroit Technologies is exploring new ways to enhance intelligent, data-driven water management. Using advanced machine learning (ML) and neural network algorithms, the research platform can analyse existing telemetry and SCADA data to detect leaks, forecast demand, and infer flow rates in areas without sensors, paving the way for more efficient, transparent municipal water systems in the future.
“South Africa's water infrastructure challenges demand smarter, data-driven solutions,” stresses Kok. “Our current R&D is focused on developing next-generation AI capabilities that will, in time, complement our existing water management technologies, which are already helping utilities reduce water losses and make informed operational decisions today.”
Addressing a National Challenge
Urban growth, vandalism, and limited monitoring capacity have severely strained South Africa's water systems. In many municipalities, leaks and pump failures are discovered only after outages occur.
Adroit Technologies' ongoing research aims to integrate new AI tools seamlessly with existing SCADA and telemetry systems to deliver predictive analytics, real-time alerts, and actionable insights, helping engineers identify hidden losses and optimise operations before crises arise.
The AI-driven ‘pseudo-metering' can infer consumption and pressure data where physical meters are missing or damaged. This innovation has the potential to help under-resourced municipalities monitor network conditions that were previously ‘data blind.'
Research with Real-World Impact
Adroit Technologies' current research is focused on developing a scalable, national-level AI framework that leverages forecasting, anomaly detection, and digital twin modelling to enhance decision-making and support more efficient water use.
A hybrid neural network architecture (CNN-LSTM) and self-healing data middleware are being designed to operate effectively even with incomplete or delayed data, a common challenge across South Africa's municipalities.
“This research is about enabling resilience,” adds Hugo Pienaar, Director of Digital Services at Adroit Technologies. “By combining AI with decades of SCADA expertise, we are helping municipalities envision how to predict issues before they happen and manage scarce water resources more efficiently.”
A Smarter, Sustainable Future
While Adroit Technologies continues to its R&D into AI-powered water management capabilities, the company already offers a proven suite of water management and SCADA solutions that empower utilities to detect leaks, optimise assets, and improve operational efficiency.
As the R&D programme progresses, these new AI capabilities will be introduced into Adroit's product range, ensuring that customers can benefit from the latest innovations in predictive maintenance, data analytics, and infrastructure optimisation, all designed to strengthen South Africa's water security and sustainability.
Distributed by APO Group on behalf of Adroit Technologies.Browse the NGAGE Media Zone for more client news articles and photographs at https://Media.NGAGE.co.za/.
Adroit Technologies Contact:
Dave Wibberley
Phone: 011 65 88100
Email: DaveW@adroit.co.za
Media Contact:
Andile Mbethe
Account Executive
NGAGE Public Relations
Phone: (011) 867-7763
Cell: 073 565 6536
Email: andile@ngage.co.za
Web: https://NGAGE.co.za
About Adroit Technologies:
Adroit Technologies is a trusted industrial software and digital solutions partner with over 35 000 installations worldwide. Backed by Mitsubishi Electric and operating as co-developer of the Mitsubishi Adroit Process Suite (MAPS), Adroit serves customers in more than 40 countries across six continents. The company specialises in SCADA systems, industrial automation, digital transformation, cybersecurity compliance, and analytics solutions for mining, water, energy, and manufacturing industries.
Website: https://AdroitSCADA.com/
Training is crucial, but feeling safe enough to speak up is critical for cyber resilience

Cybersecurity training is vital, but it's not enough on its own if your workplace culture discourages people from speaking up. Good corporate security awareness includes empowering employees to think critically, voice concerns and admit mistakes, without fear of reprisal. The secret is something all parents who've gotten their children to admit when they've done something wrong already know.
Psychological safety is an underrated part of organisational cyber resilience and yet it's essential if companies want to strengthen their cyber defences from within. “Psychological safety refers to an organisational environment where employees feel confident they can slow down to question suspicious activities, report security concerns, admit mistakes, and challenge instructions without fear of blame, punishment or professional retaliation,” explains Anna Collard, SVP of Content Strategy at KnowBe4 Africa (www.KnowBe4.com).
Jonah Berger writes in his book, Invisible Influence: The Hidden Forces that Shape Behavior:
“Parents who react negatively when their children confess to something bad they've done are inadvertently training them to lie. If a child tells you they broke a vase and you get angry and punish them severely, they learn a simple lesson: admitting the truth leads to a bad outcome.”
The question organisations need to ask themselves, even when they have implemented industry-leading security awareness training (SAT) (https://apo-opa.co/4pFnoly), is this: “What happens to employees who admit their big cybersecurity mistakes (https://apo-opa.co/3KoMiXM)? What do they expect to happen, regardless?”
What happens if employees don't feel secure?
Collard believes there are several toxic dynamics in organisations that undermine security reporting. “The most notable is the blame-first culture,” she states. “Organisations that immediately ask: ‘Who did this?' instead of ‘How can we prevent this?' create defensive behaviours where employees hide incidents.” Instead of reporting concerns that could lead to early detection, employees become silent because they fear consequences.
Another unhealthy dynamic in workplaces is when managers suffer from perfectionism. “When security is presented as binary (perfect compliance versus failure), employees avoid admitting any uncertainties or mistakes,” asserts Collard.
Having a silo mentality can also be a stumbling block. “When security teams are seen as separate from business operations, employees view them as outsiders rather than partners,” she comments. This is especially true if IT personnel fail to take employees' concerns seriously or dismiss them altogether.
Another dangerous phenomenon is when employees are confused by inconsistent messaging. “Staff don't like it when leaders preach that security is everyone's responsibility, but then exclude non-technical staff from security discussions or break the rules themselves,” Collard says.
Overcoming barriers to psychological safety
Fortunately, there are many courses of action (https://apo-opa.co/3Y3OVBi) that organisations can take to correct these unfavourable dynamics. “It's really helpful when companies implement blameless post-mortems after security incidents,” she shares.
A good example is GitLab's 2017 incident (https://apo-opa.co/48JHc1t), when a systems administrator accidentally deleted a production database, resulting in six hours of lost data. The team responded transparently, live-blogging the recovery and treating it as a learning opportunity. “A culture of openness meant the issue was addressed immediately, with no blame or cover-ups – just quick action and prevention,” comments Collard.
Collard recommends integrating security champions across all departments and celebrating reporting and learning over perfection. “It also helps when leaders model vulnerability and continuous learning,” she emphasises.
Creating positive feedback loops
Instead of coming down hard on employees who mess up, managers should frame these incidents as valuable insights about attack sophistication rather than user failure. “This can be reinforced by creating positive feedback loops as a core part of human risk management,” Collard says (https://apo-opa.co/4rsf8Hm). “Establish systems where reporting suspicious emails or activities is rewarded and celebrated, making reporting feel like a contribution rather than a confession – or even just perceived compliance burdens with no purpose.”
Her final piece of advice is for leaders to adopt a zero-trust mindset approach. “Zero-trust principles require continuous verification and questioning,” she asserts. “But this only works when people feel psychologically safe to voice their concerns.”
Digital mindfulness is another essential tool for strengthening the human layer within an organisation. “Fostering a culture of pausing and seeking help rather than rushing through work is hard in a world that moves at a relentless pace,” Collard concedes. “But it's in those high-pressure moments that we need to be most grounded and focused to avoid mistakes.”
Ultimately, she believes the most secure organisations are not those that expect perfection, but those that enable people to speak up, learn and respond quickly when something goes wrong. “Psychological safety is a critical foundation for any organisation serious about cybersecurity resilience,” Collard concludes.
Distributed by APO Group on behalf of KnowBe4.Contact details:
KnowBe4
Anne Dolinschek
anned@knowbe4.com
Red Ribbon
TJ Coenraad
tayla@redribboncommunications.co.za
4 Tips to Protect Your Payroll and Human Resources (HR) from Cybercrime

A cyberattack on payroll and HR systems can expose personal employee details and financial business information: a treasure trove for criminals and can bring companies to their knees through regulatory fines, reputational damage, and derailing operations.
"Criminals are targeting payroll and HR staff. They may trick or force them with personal info or make them think they're aiding the CEO. Ransomware attacks can encrypt payroll systems. Treating payroll and HR cybersecurity as optional is like leaving your front door wide open in a dangerous neighbourhood," says Sandra Crous, Managing Director at Deel Local Payroll, powered by PaySpace.
Securing these high-value business areas and their people reduces your business risks. With interventions ranging from personal training to using modern software, here are four tips to protect your payroll and HR from cybercrime.
1. Understand the risks faced by payroll staff
Payroll staff are high-value targets with access to sensitive information. If criminals steal that information, they can commit theft, fraud, identity theft, and much more.
Criminals target payroll staff in various ways. They can flood them with phishing attacks that steal passwords or provide unauthorised access to systems. They can launch social engineering campaigns that target staff personally. They may even find ways to exhort and coerce staff into doing their bidding. Do not underestimate the ruthlessness of online criminals that target payroll staff and the lengths they will go to.
2. Provide security training for payroll and HR staff
Once you appreciate that payroll and HR staff are the gatekeepers of important information, you can help them with security training. All staff should receive training on security fundamentals, such as good security hygiene practices and how to recognise phishing messages and scams.
Then, add training tailored to payroll staff. Let your payroll and HR staff collaborate with security trainers to build skills that match internal processes and policies. This training is not just rote—it should include psychological resilience and provide supportive, not punitive, reinforcement of solid security instincts.
3. Involve security staff
Digital security teams often have little in common with payroll or HR staff, and there is a natural tendency for them to walk separate paths. But this is a mistake. Security teams help reduce cyber risks for other parts of the business, and it is incredibly effective when security people collaborate with payroll and HR professionals.
There are various points where the two sides can connect. They can jointly discuss payroll and HR responsibilities, especially around data management. They can focus on common goals such as reducing payroll errors and maintaining compliance. They should meet regularly and create a common appreciation for the value each brings to the table. This synergy will help develop stronger security that is pragmatic and productive.
4. Use modern software
Even the best training and collaboration will crumble if the underlying software is outdated and lacks appropriate features. Isolated payroll or HR software are single points of failure that criminals can conveniently breach, encrypt, and corrupt.
Traditional payroll and HR software lack many crucial modern features and will keep falling behind. Cloud-native platforms address security shortcomings. Their account management provides nuanced and low-risk access to administrators, managers, and executives. The platform's developers automatically apply security upgrades without disrupting operations. Business and security teams have access to detailed logs and audit trails exposing criminal and fraudulent activities. Cloud-native software also enables staff to complete tasks, make approvals, and access reporting securely from anywhere.
Distributed by APO Group on behalf of Deel Local Payroll, powered by PaySpace.For media queries please contact:
Victoria Lindsay
victoria@innocomm.co.za
About Deel Local Payroll:
Deel Local Payroll, powered by PaySpace, revolutionises payroll management. It offers online, multi-country payroll and HR management for businesses from start-ups through to enterprise in over 40 African countries, the United Kingdom, the Middle East, and Brazil.
Cloud-native, Deel Local Payroll, is scalable, configurable, highly secure, and easy-to-use—delivering anytime, anywhere access. It features payroll automation, self-service features, automatic legislation and feature updates, customised reporting, and more.
Since 2024, Deel Local Payroll has been part of Deel, operating as an independent subsidiary, serving its customers through the PaySpace platform.
Egypt’s AI Revolution: Driving Toward a 7.7% GDP Boost by 2030 with Cybersecurity Empowerment!
India: Prime Minister participates in India, Brazil, South Africa (IBSA) Leaders’ Meeting in Johannesburg
Download logo
Prime Minister Shri Narendra Modi today participated in the IBSA Leaders' Meeting held in Johannesburg, South Africa. The meeting was hosted by the President of South Africa, H.E. Cyril Ramaphosa of South Africa and attended by the President of Brazil, H.E. Luiz Inácio Lula da Silva.
2. Describing the meeting as timely, Prime Minister noted that it coincided with the first G20 Summit on African soil and marked the culmination of four consecutive G20 presidencies by Global South countries, out of which the last three were by the IBSA members. This, he noted, has resulted in several important initiatives focussed on human-centric development, multilateral reform and sustainable growth.
3. Prime Minister emphasized that IBSA is not just a group of three countries but an important platform connecting three continents, three major democratic nations, and three major economies.
4. Prime Minister stressed that global governance institutions are far removed from 21st century realities. He called on IBSA to send a strong message that reform of institutions of global governance, in particular the UN Security Council, is now not an option, but an imperative.
5. On counter-terrorism, Prime Minister emphasized the need for close coordination and that there should be no room for double standards while fighting terrorism. Highlighting technology's crucial role in ensuring human-centric development, Prime Minister proposed establishing an 'IBSA Digital Innovation Alliance' to facilitate sharing of Digital Public Infrastructure like UPI, health platforms like CoWIN, cybersecurity frameworks and women-led tech initiatives among the three countries.
6. Prime Minister also emphasized IBSA's potential to contribute to the development of safe, trustworthy and human-centric AI norms. He invited IBSA leaders to the AI Impact Summit to be held in India next year.
7. Prime Minister stated that IBSA can complement each other's development and become an example for sustainable growth. He highlighted cooperation opportunities in areas such as millets, natural farming, disaster resilience, green energy, traditional medicines and health security.
8. Appreciating the IBSA Fund's work in supporting projects across forty countries in sectors like education, health, women empowerment and solar energy, Prime Minister proposed IBSA Fund for Climate Resilient Agriculture to further advance South-South cooperation. Prime Minister's full speech can be found [here].
Distributed by APO Group on behalf of Ministry of External Affairs - Government of India.